Information Security
Information Security Policy
Information security and the protection of confidential information are commitments that IOG makes to its customers, shareholders, and partners. To enhance information security protection and management mechanisms, IOG has established a dedicated team in response to the information security, allocated professional manpower and resources, clearly defining information security policies, management procedures, and standards, and declaring its determination to defend information security and promote the goal of information security—to maintain the market competitiveness of IOG and protect the interests of customers and partners.
Information Security Governance
IOG has a dedicated team, the Information Security Group, responsible for planning, monitoring, and managing information security policies and systems. The Information Security Group collaborates with the company’s IT and related units to strengthen information security protection and management mechanisms. Annually, the Information Security Group reports on cybersecurity risk management, global cybersecurity risk trends, company information security policies, plans, and execution results.
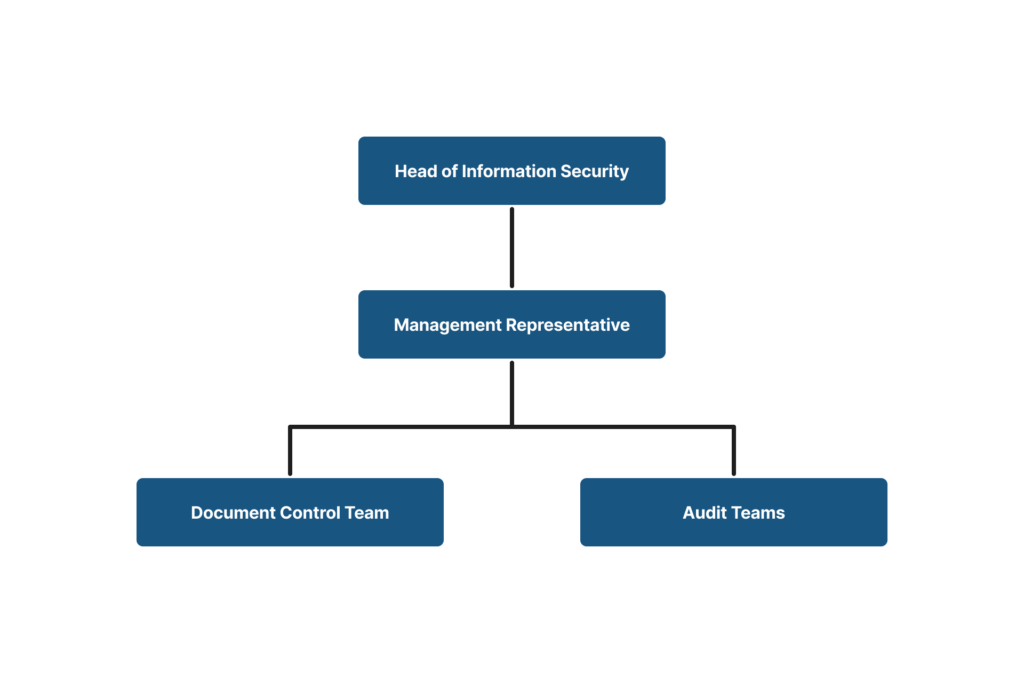
Head of information security: IOG’s Chief Financial Officer serves as the head of information security.
Management Representative: The IT manager serves as the information security management representative.
Team Members: The group includes document control and audit teams, with representatives selected by the management representative to assist in various information security activities.
Information Security Strategies and Approaches
The Information Security Group actively deepens information security and confidential information protection mechanisms to maintain the competitiveness of IOG. Following international cybersecurity standards and frameworks, it clearly defines information security policies, procedures, and standards, continuously enhances management systems and technology, and implements comprehensive risk control to achieve the company’s information security management goals. The enterprise information security organization regularly performs cybersecurity risk assessments, prioritizing based on the size of risk impact, probability, and the cost of risk mitigation. The Plan-Do-Check-Act (PDCA) method is used to structure multi-layered cybersecurity defenses and establish key performance indicators for information security. IOG has constructed an Information Security Management System (ISMS) and has obtained ISO 27001 international information security management certification since 2023, continuing to renew this certification annually. The certification scope covers the company’s IT department ERP system development, maintenance, basic network infrastructure, and information equipment maintenance information activities management.
Key Focuses of Information Security Management
To prevent and reduce external cybersecurity risks, IOG implements and continuously updates rigorous cybersecurity measures, such as deploying advanced virus scanning tools to prevent the risk of virus infections on company computers; enhancing network firewalls and network control to prevent computer viruses from spreading across different departments; deploying antivirus measures and advanced malware detection solutions on company computers; improving cybersecurity deployment time to enhance data center security; and establishing and regularly reviewing cybersecurity performance indicators. New technologies are introduced to strengthen data protection; phishing email detection is enhanced with regular employee awareness testing; an integrated automated cybersecurity maintenance platform is established, and cybersecurity incident detection and handling automation are strengthened; cybersecurity attack response procedures are continuously drilled. The annual cybersecurity implementation focus includes:
- Network security control
- Asset management and data protection
- Access control
- Computer operations security management
- Personnel and physical security
- Application security
- Cybersecurity incident handling and management
- Personnel cybersecurity management and education promotion
- Asset risk management
Information Security Incidents and Reporting Procedure
IOG has established group-level Risk Management Group to implement enterprise risk management mechanisms and cybersecurity incident handling standard procedures, clearly defining related processes and measures, including cybersecurity incident reporting procedures, assigning responsible personnel to handle major information security incidents, assessing losses incurred, and further necessary response measures, evaluating the impact of cybersecurity risks on the company’s financial and operational aspects, and corresponding measures.



